







What Is HITRUST and Why Does It Matter in Healthcare?

Healthcare organizations face an unprecedented challenge: protecting sensitive patient data while navigating an increasingly complex regulatory landscape. As cybersecurity threats continue to evolve, the consequences of a breach extend far beyond financial losses. For instance, a breach damages patient trust and has the potential to compromise care quality.
This complexity has led many healthcare leaders to adopt HITRUST certification as their comprehensive approach to security and compliance. Rather than managing multiple frameworks separately, HITRUST provides a single solution that demonstrates compliance with the Health Insurance Portability and Accountability Act (HIPAA), National Institute of Standards and Technology (NIST) guidelines, and dozens of other regulatory requirements through a single, certifiable process.
For healthcare chief information officers (CIOs) and IT leaders, understanding what HITRUST offers—and why it's becoming an industry standard—is essential for building a resilient, future-ready organization.
What Is HITRUST?
Founded in 2007 and originally known as the Health Information Trust Alliance, HITRUST has developed a cybersecurity framework specifically for organizations that handle sensitive information, particularly in healthcare. HITRUST created the Common Security Framework (CSF) to address the complexities of healthcare data protection and regulatory compliance.
The HITRUST CSF integrates requirements from multiple sources—including HIPAA, the NIST Cybersecurity Framework, ISO/IEC 27001, Payment Card Industry Data Security Standard (PCI DSS), and General Data Protection Regulation (GDPR)—into one cohesive framework. This integration allows organizations to demonstrate compliance with numerous standards through a single assessment process rather than managing separate audits and certifications.
HITRUST updates the framework regularly, using artificial intelligence, to incorporate emerging threats and evolving compliance requirements. This ensures organizations stay current with the latest cybersecurity standards and regulatory changes.
How Is HITRUST Different From HIPAA Compliance?
Many healthcare organizations assume they’re sufficiently protected as long as they comply with HIPAA regulations, but HITRUST offers a more comprehensive approach to security.
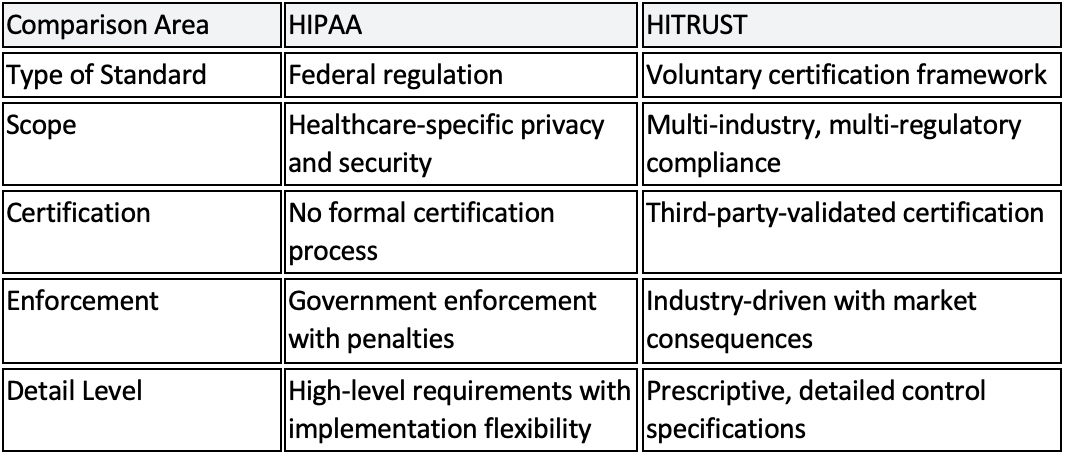
HIPAA
- Type of Standard: Federal regulation
- Scope: Healthcare-specific privacy and security
- Certification: No formal certification process
- Enforcement: Government enforcement with penalties
- Detail Level: High-level requirements with implementation flexibility
HITRUST
- Type of Standard: Voluntary certification framework
- Scope: Multi-industry, multi-regulatory compliance
- Certification: Third-party-validated certification
- Enforcement: Industry-driven with market consequences
- Detail Level: Prescriptive, detailed control specifications
HITRUST provides a structured framework that supports HIPAA compliance by translating its broad guidelines into specific, measurable security controls. It helps healthcare organizations go beyond regulatory requirements with a unified approach to risk management and data protection.
Key Components of the HITRUST CSF
The HITRUST CSF addresses security and privacy controls across multiple domains that organizations must implement to achieve certification, including:
- Access control and identity management: Detailed specifications for user authentication, authorization, and privilege management
- Data protection and encryption: Requirements for protecting data at rest, in transit, and during processing
- Incident response and disaster recovery: Structured approaches to identifying, responding to, and recovering from security incidents
- Risk management and mitigation practices: Systematic methods for identifying, assessing, and addressing information security risks
- Security awareness training: Comprehensive education programs for all organizational personnel
- Network protection: Controls for securing network infrastructure and communications
- Business continuity planning: Strategies for maintaining operations during disruptions
- Vendor and third-party oversight: Management of risks introduced through external relationships
- Continuous monitoring and remediation protocols: Ongoing surveillance and improvement of security posture
The framework operates on a maturity model with five levels: policies, procedures, implementation, measurement, and managed practices. This structure allows organizations to demonstrate not just that controls exist, but that they’re effectively implemented and continuously improved.
Why HITRUST Matters for Healthcare in 2025 and Beyond
Healthcare organizations face mounting pressures that make HITRUST certification increasingly valuable for strategic operations and risk management.
Rising cybersecurity threats and legal exposure
Ransomware attacks on healthcare organizations increased 278% from January 2018 through September 2023, according to the Department of Health and Human Services Office for Civil Rights. A 2023 report by IBM, which analyzed data breaches occurring between March 2022 and March 2023, stated that breaches in healthcare were the most expensive, with an average cost per incident of $10.93 million—a 53.3% increase over the previous three years.
Phishing campaigns specifically target healthcare workers, exploiting their access to valuable patient data. Meanwhile, insider threats—whether malicious or accidental—continue to represent a significant risk.
By implementing threat-adaptive assessments that evolve with the changing risk landscape, HITRUST takes a proactive approach to cyber defense. Organizations with a HITRUST certification had a 99.41% breach-free rate in 2024, according to HITRUST.
Increasing regulatory and accreditation pressure
Healthcare organizations must navigate requirements from HIPAA, NIST, state privacy laws, Centers for Medicare & Medicaid Services (CMS) conditions of participation, and, increasingly, international standards for global operations. Each of these frameworks has unique requirements, creating a complex compliance scenario that strains organizations’ resources and increases the risk of gaps.
HITRUST streamlines this challenge by mapping controls to dozens of sources, making it possible to demonstrate compliance with multiple frameworks through just one assessment. This approach reduces redundant efforts while ensuring necessary compliance.
Streamlined vendor and partner compliance
Large health systems, payers, and technology partners increasingly expect HITRUST certification from vendors and affiliates. This trend reflects the shared responsibility model in healthcare, in which data breaches at third-party vendors can impact the primary organization's reputation and regulatory standing.
HITRUST certification helps organizations demonstrate alignment with these requirements efficiently, reducing the time and resources needed to complete vendor questionnaires and security assessments for multiple partners.
Organizational reputation and patient trust
Data breaches in healthcare receive significant media attention and regulatory scrutiny, often resulting in long-term damage to an organization’s reputation. Patients, providers, and partners often view security incidents as indicators of overall operational quality and trustworthiness.
HITRUST certification provides a credible, third-party-validated demonstration of an organization’s commitment to data protection. This certification differentiates organizations in competitive situations and builds confidence among stakeholders who rely on the organization’s security practices.
The HITRUST Certification Process: Overview for Healthcare Leaders
Achieving HITRUST certification typically takes six to 12 months, depending on the organization’s operations and structure, and the desired certification level. Healthcare leaders should approach this as a strategic initiative that requires executive support and cross-functional collaboration.
1. Scoping and readiness assessment
The first step is for organizations to define the scope of their assessment and conduct a readiness evaluation to identify current gaps. This phase involves mapping existing controls to HITRUST requirements and determining which certification level (e1, i1, or r2) aligns with the organization’s risk profile and stakeholder expectations.
2. Gap analysis and remediation
The gap analysis reveals specific areas where current controls fail to meet HITRUST standards. The next step is to develop remediation plans to address these gaps, often requiring updates to policies, procedures, technical controls, and training programs.
3. Audit preparation and control implementation
At this point, organizations implement the required controls and gather evidence demonstrating their effectiveness. This phase requires coordination across IT, compliance, risk management, and operational teams to ensure the controls function as designed and to produce appropriate documentation.
4. Validated assessment (third-party audited)
A HITRUST-authorized external assessor conducts the formal assessment, reviewing evidence and testing control effectiveness. This independent validation ensures consistency and credibility in the certification process.
5. Certification and ongoing maintenance
Upon successful completion of the previous steps, organizations receive a HITRUST certification that is valid for one year (i1) or two years (r2). Maintaining the certification requires ongoing monitoring, annual reviews, and demonstration of continued control effectiveness.
6. Annual review and recertification (every 2 years)
Organizations must complete interim assessments and full recertification to maintain their status. This process ensures controls remain effective, even as threats and regulations evolve.
How HITRUST Impacts Workforce Education and Credentialing Practices
HITRUST certification goes beyond technical controls, encompassing workforce readiness and ongoing education requirements.
Mandatory staff training
HITRUST requires documented security awareness training for all personnel who have access to sensitive information. This training must cover current threat landscapes, organizational policies, and incident response procedures. Organizations are required to track completion rates, assess understanding, and provide regular updates as threats evolve.
Role-based competency tracking
Different roles within healthcare organizations require distinct training and competency validation. For example, clinical staff need training on privacy practices and secure communication, while IT personnel require technical security training and incident response procedures. Administrative staff need training on social engineering recognition and data handling practices.
To achieve and maintain HITRUST certification, organizations must document role-specific competency requirements and keep records of both staff qualifications and ongoing education.
Continuous education
HITRUST certification depends on real, measurable engagement rather than static policy documents. Organizations must demonstrate that their staff keeps current on security awareness and can effectively respond to evolving threats and changing procedures.
By integrating security training with existing professional development programs, healthcare organizations can ensure their staff maintains security awareness while clinicians maintain both clinical competencies and security awareness.
How HealthStream Helps Healthcare Organizations Align With HITRUST
HealthStream provides comprehensive solutions that support HITRUST readiness through integrated education, credentialing, and compliance management capabilities.
Security awareness and compliance training modules help organizations meet HITRUST requirements for documented staff education. These modules cover current threat landscapes, regulatory requirements, and organizational policies with tracking capabilities that demonstrate ongoing compliance.
Role-based learning paths and assessments enable organizations to customize training based on specific job functions and access levels. Healthcare organizations can ensure clinical, administrative, and technical staff receive appropriate education while maintaining documentation required for HITRUST certification.
Credentialing and performance tracking capabilities support the competency documentation requirements inherent in HITRUST frameworks. Organizations can link security training completion to credentialing processes, ensuring staff maintain both professional qualifications and security awareness.
Policy management tools help organizations maintain the documented policies and procedures required for HITRUST compliance while making sure staff have access to current information and acknowledge policy updates.
These integrated capabilities reduce the administrative burden of HITRUST compliance while enabling organizations to demonstrate the workforce readiness that certification requires.
Building Your HITRUST-Ready Organization
HITRUST represents more than a compliance checkbox. It’s an enterprise-grade framework that helps future-proof healthcare organizations against evolving risks, regulatory complexity, and digital transformation challenges. The certification process creates systematic approaches to risk management that strengthen operational resilience while giving organizations the opportunity to demonstrate their commitment to data protection.
Healthcare leaders can begin by assessing their organization’s compliance gaps and engaging with internal stakeholders to build support for the certification process. These conversations should include IT leadership, compliance teams, risk management, and clinical operations to ensure readiness throughout the organization.
HealthStream’s education and credentialing solutions provide the workforce development foundation HITRUST certification requires. By integrating security awareness training with their professional development programs, organizations can build a culture of security preparedness that supports not only certification requirements but also operational excellence.
The investment in HITRUST certification pays dividends through reduced cybersecurity insurance costs, streamlined vendor relationships, enhanced competitive positioning, and, most importantly, the confidence that comes from implementing proven security practices in an increasingly complex threat environment.
