







It’s Time to Switch to Longer Passwords

Robin L. Rose, MBA
Randy L. Carden, EdD
HealthStream
Data breaches are creating massive headaches for the healthcare industry. They not only have the potential to disrupt patient care, but they can also lead to millions (and sometimes billions) of dollars in reparations, ransom, and HIPAA fines. Healthcare organizations are working diligently to address these threats, but the truth is it takes the cooperation of every healthcare employee to ensure a secure working environment. Organizations can be at the mercy of their weakest password. Are you doing all you can to keep your company safe?
Cybersecurity breaches
Data breaches have become an enormous problem for healthcare organizations over the past 14 years. The chart below, which is based on HIPAA records, shows the upward trend in breaches the healthcare industry has experienced during this time (Murray-Watson, 2023).
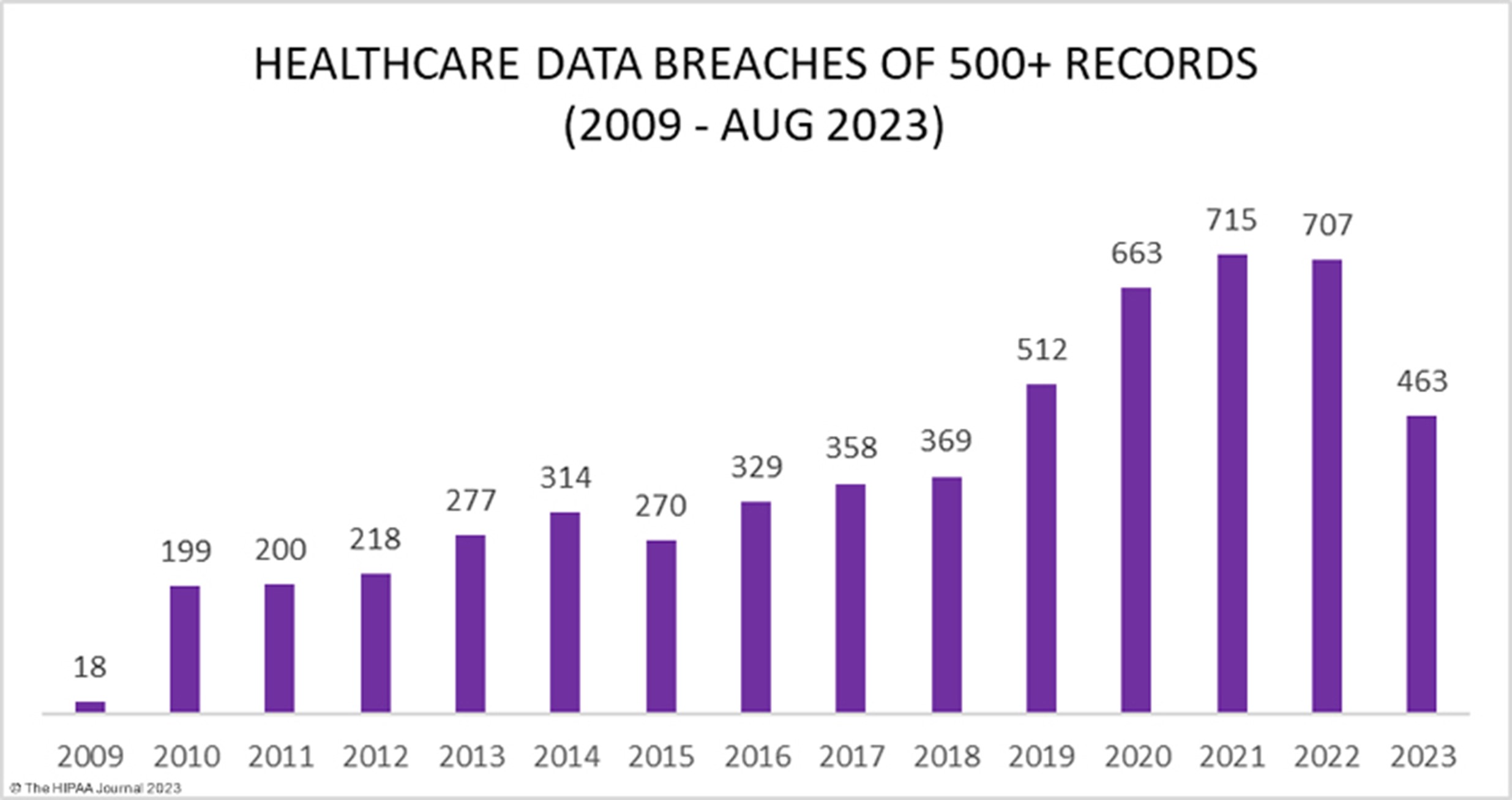
These breaches have resulted in the exposure or impermissible disclosure of 382,262,109 healthcare records which equates to more than 1.2x the population of the United States. In 2018, healthcare data breaches of 500 or more records were being reported at a rate of around 1 per day. Fast forward 5 years and the rate has more than doubled. In 2022, an average of 1.94 healthcare data breaches of 500 or more records were reported each day (Murray-Watson, 2023).
High value data
The richness of data housed by healthcare entities has been cited as a primary reason that healthcare is susceptible to high data breach and financial risks. Healthcare organizations usually possess a high volume of sensitive data. Data containing names, date of birth, social security number, address, and credit card information are abundant in healthcare records. Moreover, hackers prefer focusing on healthcare organizations because healthcare data is more valuable than data from other industries in the black market. An electronic health record (EHR), for instance, is worth between 10 and 100 times more than credit card information in the black market (Bhuyan, 2020).
The impact of the pandemic
The COVID-19 pandemic created a unique environment that fueled the incidence of data breaches in the healthcare industry. COVID-19 has been dubbed the world's biggest cybersecurity threat, with healthcare and banking industries being the most vulnerable to cyber-attacks (Nabe, 2023). Several factors contributed to this increase in the number of cybersecurity breaches and cybercrime attacks since 2019. The first factor is the increased demand for healthcare services due to the pandemic, which has led to a strain on resources and reduced the amount of time and resources available to dedicate to cybersecurity measures. This has made healthcare organizations more vulnerable to cyberattacks, as they have been unable to protect themselves adequately from cybercriminals.
The shift to remote working due to the pandemic has also increased the risk of cybercrime attacks, asremote workers need to be adequately trained in cybersecurity best practices and may be using insecure devices or networks vulnerable to attack. According to a recent study by Deloitte, some 47% of individuals fell for a phishing scam while working from home (Nabe, 2023). Cyber-attackers see the pandemic as an opportunity to step up their criminal activities by exploiting the vulnerability of employees working from home and capitalizing on people's strong interest in coronavirus-related news (e.g. malicious fake coronavirus related websites). Finally, the increase in the use of telemedicine due to the pandemic has created new opportunities for cybercriminals, as it has increased the amount of data being transmitted over the internet, which cybercriminals can intercept and exploit.
Weak and compromised passwords
"Compromised passwords are one of the most concerning risks for hospitals and other healthcare organizations," reports Karin Balsley, Senior Director of Information Security at HealthStream. In fact, over 80% of data breaches are due to compromised passwords in some capacity (Enzoic, 2023).
Passwords are one of the most difficult areas in which to enforce effective security because they are selected by the user. According to Google, 52% of people openly admit to reusing passwords across multiple, if not all, accounts and sites. And like most people, healthcare staff reuse passwords. Even if an employee has a very complex password, reusing it on multiple sites can create a major vulnerability (Enzoic, 2023).
Weak passwords are also a major issue. Clinical staff often follow the path of least resistance when it comes to passwords. They often opt for passwords that are simple to type in and easy to remember. This includes creating passwords that use the name of the hospital or common dictionary words with simple substitutions. Unfortunately, cybercriminals are aware of typical substitution patterns, so these are very risky habits.
Password sharing is also a significant issue in hospitals and other healthcare settings. According to a study by Healthcare IT News, 73.6% of surveyed hospital staff had obtained the password of another medical staff member.
"Most incidents of unintended access start with an individual account that has an easily guessed pass-word," says Matthew Wilson, VP, Technology - Platform at HealthStream. "Organizations have established data access policies, and it is critical to adhere to those policies. It is also important to apply a common-sense approach to security. When it comes to people's behavior regarding IT systems, people should ask themselves: ‘Would I be comfortable if an employee of my bank did the same thing?'"
Most hacked passwords
Commonly used passwords are often weak and easily hacked. According to SafetyDetectives.com, fifty percent of the most common passwords in the U.S. are also among the most hacked (Dydra, 2023). The cybersecurity firm analyzed more than 18 million passwords worldwide to identify the top 10 most hacked passwords:
- 123456
- password
- 12345678
- 1234567
- qwerty
- 654321
- 111111
- 123123
- 1234567890
- Iloveyou
Using medical terms in passwords
A team from Cybernews examined 56 million breached and leaked passwords in 2022.The researchers discovered medical terms in breached and leaked passwords. Among the most commonly used were "ache" (31,287 times), "liver" (17,360), and "heart" (12,707).Source: Egle Kristopaityte, 2022
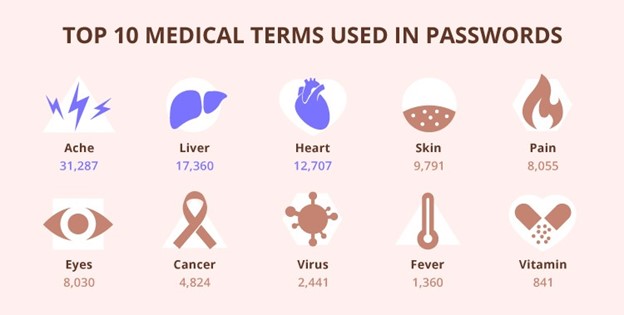
Source: Egle Kristopaityte, 2022
Making it hard for the hackers
Hive Systems, a Richmond, Virginia based cybersecurity firm, has calculated the amount of time it takes a hacker to decipher a password based on its complexity. Their conclusions are that a simple, numbers only 4-character password can be instantly deciphered given the state of hacker technology in 2023. However, an 18-character password using a combination of numbers, letters, and symbols might take 2 quadrillion years.

Maximum time required to crack randomly generated passwords with 5,000 iterations using an RTX 4090.
As the above table shows, the longer the password, the longer it takes for a hacker to decipher it. "To me, length trumps complexity every time," says Balsley. "I recommend employees use a pass phrase instead of a password. Something like, ‘I went to the store' written as one word with some special characters mixed in—not just an exclamation point at the end."
Hardening your passwords
Here are some guidelines to consider in hardening your own passwords: (Password Protection, 2020)
- Consider using a password-manager program to keep track of your passwords.
- Develop mnemonics to remember complex passwords.
- Do not use passwords that are based on personal information that can be easily accessed or guessed.
- Do not use words that can be found in any dictionary of any language.
- Use different passwords on different systems and accounts.
- Use the longest password or passphrase permissible. The industry standard for minimum password length is eight characters, and a mix of letters, numbers, and special characters is preferred.
- Avoid using passwords that are easy to guess based on region. For example, if cybercriminals are looking to make a quick, effortless attack on Boston-area hospitals, they are likely to guess passwords like "redsox," "bosox," or "patriots." Names of sports teams should be off-limits. Likewise, names of public figures or famous athletes from that particular region also make for easy-to-guess passwords. "Lebron23" and "Brady12" appear high on the list of commonly used passwords.
- Change passwords frequently—preferably at least every 90 days.
- Keep anti-virus software on your computer up-to-date.
Beyond just passwords--multi-factor authentication
Multi-factor authentication (MFA; two-factor authentication, or 2FA) is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism. MFA protects personal data—which may include personal identification or financial assets—from being accessed by an unauthorized third party that may have been able to discover, for example, a single password.
According to Jeff Cunningham, Sr. VP & Chief Technology Officer at HealthStream, it is important to implement security measures in addition to strong passwords. "The direction we want to go, is to have strong passwords, ensure that we are changing passwords regularly, and are using multi-factor authentication on top of that.
"Certainly, the first step is securing the complexity of the password. How hard do we make it for a hacker to break that password? I know it sounds simple, but basically the greater length and the more variety that we have in the password, the harder it is to break."One of the best ways to ensure password hardening is to make sure that we are not relying completely on the password. I am going to look at multiple ways of securing that password, and multifactor authentication is a way of doing that That's basically saying that not only am I relying on the password, but for you to get access to a system, I am going to validate through some other mechanism that you are who you say you are."
In conclusion, hackers are on the prowl, wreaking havoc wherever possible. As employees in the highly targeted healthcare industry, we need to do our part to keep our organizations safe. It is time to harden those passwords.
References
Bhuyan, Soumitra Sudip et al., "Transforming Healthcare Cybersecurity from Reactive to Pro-active: Current Status and Future Recommendations," Journal of Medical Systems (2020) 44:98, https://pubmed.ncbi.nlm.nih.gov/32239357/.
Burrell, Darrell Norman, "CYBERSECURITY IN HEALTHCARE THROUGH THE 7-S MODEL STRATEGY," Scientific Bulletin, 2023, Vol. 28 Issue 1, https://intapi.sciendo.com/pdf/10.2478/bsaft-2023-0003.
Dyrda, Linda, "10 most hacked passwords," Becker's Hosppital Review, June 28th, 2023, https://www.beckershospitalreview.com/cyber security/10-most-hacked-passwords.html.
Employee Password Security in the Healthcare Sector, Enzoic, Accessed September 2023, https://www.enzoic.com/blog/employee-password-security-in-the-healthcare-sector/.
Kristopaityte, Egle, "Weakest Passwords of 2022: Most Often Used Medical Terms," November 22, 2022, Weakest Passwords of 2022-Most Often Used Medical Terms.docx (sharepoint.com).
Murray-Watson, Rebecca, Healthcare Data Breach Statistics, The HIPAA Journal, September 2023, HIPAA Journal, https://www.hipaajournal.com/healthcare-data-breach-statistics/.
Nabe, Cedric, "Impact of COVID-19 on Cybersecurity," Deloitte, accessed September 20, 2023, https://www2.deloitte.com/ch/en/pages/risk/articles/impact-covid-cybersecurity.html.
Neskey, Corey, "Examining the LastPass Breach Through our Password Table," Hive Systems, September 13, 2023, https://www.hivesystems.io/blog/examining-the-lastpass-breach-through-our-password-table.
"Password protection: Guarding against surge in attacks amid COVID-19," Revenue Cycle Advisor, June 2020, https://revenuecycleadvisor.com/search/node/Password%20protection%3A%20Guarding%20against%20surge%20in%20attacks%20amid%20COVID-19?type=All.
